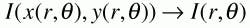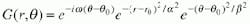Spotlight on Advanced Technology: Wavelet analysis ensures accurate recognition of iris patterns
Research in wavelet-analysis algorithms, pioneered at the University of Cambridge, has enabled biometric systems to identify people by their iris patterns.
By Andrew Wilson,Editor at Large
To measure the physiological or behavioral characteristics needed to verify a person's identity, biometric identification (ID) systems are using fingerprints, retinal and iris scanning, hand geometry, voice patterns, and facial-recognition techniques. Installed in many military security systems, biometric systems are now finding other applications in Internet security, automatic teller machines (ATMs), forensic identification, and credit-card authentication.
A credit-card personal identification number (PIN) was one of the first identifying techniques that allowed an ID system to automatically acknowledge a user. But such methods only identify the PIN number, not the person. Biometric ID systems, on the other hand, use a unique identifier, such as a human iris, to automate the person-verification procedure.
"The prospect of using the human iris for identification was first suggested by ophthalmologists, who noted that the pattern of the iris remained unchanged in clinical photographs taken over several decades," says Chris Seal, a researcher with British Telecommunications (London, England). The iris consists of a fibrous structure that stretches as the pupil diameter varies. "While some iris features such as color are inherited, the detail in the texture is established by random processes before birth," says Seal.
FIGURE 1. Zones of analysis are established on the human iris in a projected pseudopolar coordinate system that maintains reference to the same regions of iris tissue regardless of papillary constriction and overall iris image size. Demarcations of the zones of analysis are based on a fixed partitioning of the polar-coordinate system. For any person's eye, the radial scaling used depends on the pupil diameter relative to the outer boundary of the iris.
In 1991, a strategy was developed for deriving a set of characteristic parameters from an iris texture using wavelet analysis by John Daugman, professor in the Computer Laboratory of Cambridge University (Cambridge, England). To commercialize the method, Daugman and his colleagues formed IriScan (Marlton, NJ), a company that holds the exclusive worldwide patents on this iris-recognition concept. Today, companies such as Sensar (Moorestown, NJ), Oki America (Hackensack, NJ), NCR Corp. (Dayton, OH), and Diebold (North Canton, OH) are licensing the iris technology for the development of various people-recognition systems.
The eyes have it
"Iris analysis begins by establishing whether an iris is visible in a captured video image and then locates its inner and outer boundaries," says Daugman. "Because of the circular geometry of the iris, these tasks can be accomplished for a raw input image by using an algorithm to search over the image for the maximum in the partial derivative of a contour integral," he says.
The algorithm operators behave as a circular edge detector that searches iteratively for a maximum contour integral derivative with increasing radius at successively finer scales of analysis.
Iris analysis begins by establishing whether an iris is visible in a captured video image and then locates its inner and outer boundaries. Equation 1 shows a circular edge detector, that searches iteratively for a maximum contour integral derivative with increasing radius at successively finer scales of analysis. The iris image is then remapped into a dimensionless nonconcentric polar coordinate system by Equation 2, where x and y represent linear combinations of the boundary points between the inner and outer parts of the iris. After this mapping of the iris tissue, its textural pattern is encoded using complex-valued 2-D Gabor wavelets (see figure left), as described in Equations 4-7 below. Such wavelets are complex exponentials windowed by bivariate Gaussians. They are used to demodulate the iris data to set bits as vertices in the complex plane, the ensemble of that data creates a unique iris code.
null
At first, the blurring factor (sigma) is set for a coarse scale of analysis so that only the very pronounced circular transition from iris to white sclera is detected. After this strong circular boundary is more precisely estimated, a second search begins within the confined central interior of the located iris for the fainter pupillary boundary. This search uses a finer convolution scale and a smaller search range to define the paths of contour integration.
Once the inner and outer boundaries of the iris are localized, a dimensionless coordinate system maps the image so that it is invariant to the changes in constriction of the pupil, overall iris image size, camera zoom factor, and distance to the eye. This coordinate system is pseudopolar and compensates automatically for the stretching of the iris tissue as the pupil dilates.
Zones of analysis are established on the iris in the projected pseudopolar-coordinate system that maintains reference to the same regions of iris tissue regardless of both pupillary constriction and overall iris image size. "This coordinate system is not necessarily concentric," says Daugman, "because for most eyes the pupil is not central in the iris."
The stretching of the iris from constriction of the pupil is modeled by the coordinate system as the stretching of a homogeneous rubber sheet with the topology of an annulus anchored along its outer perimeter and with tension controlled by an off-centered interior ring of variable radius. The homogeneous rubber-sheet model assigns to each point in the iris both radial and angular coordinates. The remapping of the iris image from an x-y coordinate system to the dimensionless nonconcentric polar coordinate system is performed by another algorithm operator where x and y are linear combinations of the boundary points between the inner and outer part of the iris.
The final step, before actual encoding of the iris features begins, is to detect the eyelids and fit their boundaries so that they can be excluded from contaminating the iris code. Even eyelashes are detected and excluded from affecting the iris code. The eyelids are located, once again, by the derivatives of contour integrals, and their contours are fit by splines (see Fig. 1).
Wavelet analysis
Two-dimensional (2-D) Gabor wavelets are used to extract information from these images. Originally proposed by Daugman as a framework for understanding the receptive field properties of neurons in the brain's visual cortex, Gabor wavelets provide the maximum possible resolution for both information about the orientation and spatial-frequency content of local image structure and for position. These properties are useful for texture analysis because of the 2-D spectral specificity of texture and its variation with 2-D spatial position.
Gabor wavelets possess some interesting characteristics. In addition to performing multiresolution analysis, some researchers have modeled biological vision systems using Gabor functions. As a complex exponential modulated by a Gaussian function, the Gabor function can be described in the dimensionless polar-coordinate system.
null
By evaluating, at one scale of analysis, the signs of both the real and imaginary parts of the image projections from a local region of the iris image onto a 2-D Gabor wavelet, a 256-byte code can be developed that is a unique description of a person's iris (see box and accompanying equations on p. 31). Each bit of this so-called iris code is computed by performing a coarse phase quantization of the local texture signal by approximating it as one vertex (0,0), (0,1), (1,0), or (1,1) in the complex plane.
Says Daugman, "The time required for computing a complete iris code of 2048 such paired bits (256 bytes) on a RISC-based CPU, once an iris has been located within the image, is about 100 ms with optimized integer code. Better still, an exact match need not be found, as the identification algorithm can accept up to a 33% mismatch and still make a high-confidence identification. This robustness is achieved because the remaining code still contains a vast number of characteristic features of the iris."
Biometric applications
At present, the technology developed at the University of Cambridge is being used in a number of products in Europe, Japan, and the United States. In Europe and Japan, the main applications of iris identification are ATMs and security systems. For example, last year in England, the Nationwide Building Society (Swindon, England) introduced an iris-recognition application within its cash-dispensing machines. Joining with the NCR Financial Solutions Group, Nationwide is testing customer reaction to the technology and its commercial viability. The technology, licensed to Sensar from IriScan, has been integrated by NCR into a Nationwide cash machine and at a branch counter of Nationwide's head office in Swindon.
FIGURE 2. Oki Electric is field testing an access-control system developed for Suruga Bank that automatically obtains persons' iris images as their biometrics signatures. Using a video camera, Oki's recognition system obtains an image of an iris at a distance of up to 3 ft away that is then encoded as an Iris Code and stored for future reference.
During operation, the recognition system uses a camera to capture a digital record of a user's iris. No form of light or laser beam is shone into the eye; the iris pattern is fully registered only by the camera. Within seconds, the system can verify the user's iris record from a central database or a smart card. "Using the iris)151;the one part of the body that is unique and constant throughout a person's life—also affords the greatest level of security," says Brian Davis, chief executive officer of Nationwide.
Beyond its use in financial transactions, iris recognition is playing a key role in other applications where a person's identity must be established or confirmed. These include passport control, electronic commerce, entitlements payments, premises entry, access to privileged information, authorizations, forensic and police applications, and computer login.
In Japan, Oki Electric is field-testing an access-control system developed for Suruga Bank that is capable of automatically obtaining iris images of people as biometrics signatures to ensure authorized access to the Suruga Bank's main computer room. Using a standard video camera, Oki's iris-identification system obtains an image of a person's iris at a distance of up to 3 ft (0.91 m; see Fig. 2). The iris pattern is then encoded into an iris code by Daugman's algorithms and stored for future reference. When verifying a person's identity, data are retrieved and matched to the person's iris image using 256 bytes per eye. The entire identification process takes less than one second, with a 1/1.2 million margin of error.
Biometric performance
Biometric-identification performance can be characterized as a graph of two histograms (see Fig. 3). One histogram shows comparisons between different images of the same iris; the other histogram shows comparisons between different irises. Because the histograms are well separated in Hamming distance and have minimal overlap, it is possible to distinguish the "same" versus "different" iris patterns.
FIGURE 3. In iris recognition, the similarity measure of two iris patterns is the fraction of bits in two Iris Codes that disagree. The left distribution curve shows the results when different images of the same eye are compared—about 10% of the bits might differ. But when Iris Codes from different eyes are compared, the fraction of disagreeing bits is very tightly packed around 45%, as shown in the right distribution curve. Because of the narrowness of this packed distribution, identification decisions can be made with very high levels of confidence. For example, the odds of two different irises agreeing just by chance in more than 75% of their Iris Code bits are only one in 1016.
One measure of the decision-making power of an iris-identification system can be defined as the separation between the mean values of the two histogram distributions divided by the square root of their average variance. According to tests conducted by British Telecommunications, the decision-making capability for iris recognition is far higher than for any other known biometric.
"Today there is renewed interest in reliable, rapid, and nonintrusive means for automatically recognizing the identity of people," says Daugman. "Security breaches in access to restricted areas at airports have contributed to terrorism; and credit-card fraud now costs $6 billion annually," he says.
Company Information
British Telecommunications
London, England EC1A 7AJ
(44) (0171) 356-5000
Fax: (44) (0171) 356-5520
Web: www.bt.com
Diebold
North Canton, OH 44720
(330) 490-4000
Web: www2.diebold.com
IriScan
Marlton, NJ 08053
(800) 333-6777
Fax: (856) 797-6877
Web: www.iriscan.com/index.htm
LG Corporate Institute of Technology
Seoul 137-724, Korea
(82) 2-526-4185
Fax: (82) 2-576-84189
E-mail: [email protected]
Web: www.lgeus.com
Nationwide Building Society
Swindon, England
(44) 0345 30 20 10
Web: www.nationwide.co.uk/
NCR Corp.
Dayton, OH 45479
(937) 445-5000
Web: www3.ncr.com/fact_sheet. html#Who We Are
Oki America
Hackensack, NJ 07601
(201) 646-0011
Fax: (201) 646-9229
Web: www.oki.com
Sensar
Moorestown, NJ 08057
(856) 222-9090
Fax: (856) 222-9020
Web: www.sensar.com/contacts/contacts.stm
University of Cambridge
Cambridge, England CB2 3QG
(44) 1223 334501
Fax: (44) 1223 334679