Personal-verification technologies use biometrics for identification
Personal-verification technologies use biometrics for identification
By Shari L. S. Worthington, Contributing Editor
During the last decade, a fast-growing science called biometrics has dominated developments in the security field. In effect, biometrics has been evolved from a statistical science to practical applications in personal identification. In the transition, it has spawned a repertoire of identification and verification techniques, such as voice printing, retinal scans, photo imaging, digital signatures, finger imaging, smart cards, face recognition, and DNA matching. These techniques have emerged because of the marked improvements made in microprocessor technology, which can now meet the high-speed demands of biometric algorithms.
To assess the merits of personal-verification systems, Alan Westin, professor of public law and government at Columbia University (New York City), analyzed the results of a public-opinion survey for The National Registry Inc. (Tampa, FL), a developer of fingerprint-recognition systems. In a published report, Westin said that accurate identification is vital in criminal investigations, civil court proceedings, immigration controls, identification of disaster and amnesia victims, and for a range of business and social applications.1 These applications include authenticating checks, using credit cards, accessing computer systems, identifying people for government benefits, and controlling access to secured areas.
Survey respondents gave high approval to finger imaging as a means of combating deception and for checking job applicants for relevant criminal convictions. Even with the public`s vocal concern for privacy, they also did not envision finger imaging as stigmatizing or unfair.
Fingerprint recognition
Finger imaging or fingerprint recognition involves optically or digitally scanning a fingertip, entering a digitized record in a computer database, and comparing the finger image to another for verification or identification. Identifying individual finger patterns depends on an analysis of small ridge endings on the finger known as minutiae. The padded part of an average finger contains between 40 and 60 minutiae, whose location and position can be analyzed. Because each fingerprint is unique, the composition or pattern of a person`s minutiae is also unique. To speed the process, designers of most fingerprint-recognition systems limit the number of minutiae points analyzed to a few small areas within the print.
Mytec Technologies (Toronto, Ont., Canada) builds fingerprint-recognition systems that are commonly used in electronic commerce applications and that restrict access to databases or restricted areas.
According to Keith Clemons, Mytec director of sales and marketing, regardless of the results of The National Registry survey, the legal and moral issues associated with a person`s right to privacy are of utmost importance. "A citizen`s right to privacy must be balanced against the obligation of the state to protect the physical and financial security of society at large," says Clemons. "The fingerprinting of welfare recipients is a means to reduce fraud. But the need to prove eligibility for welfare benefits by fingerprinting is viewed by many as undesirable," he says.
Mytec`s solution is a process it calls "biometric signature encryption," which uses the information contained in a person`s finger pattern to optically code a personal identification number (PIN). This number serves as the person`s unique and private signature and can be decoded only by the appropriate finger pattern. The system performs a search to ensure that the same signature information has not previously been used, thereby eliminating fraud. To override privacy issues, biometric signature encryption does not involve storing fingerprints or providing information that can be used to generate or retrieve finger patterns. Coding PINs as finger patterns ensures that a person`s privacy is maintained while the state preserves its financial security.
Mytec`s first biometric system, Zebra, was based on an optical computer capable of parallel processing. In operation, the system could recognize complex and intricate finger patterns in about 1 ns, approximately one billion times faster than a Pentium microprocessor.
Mytec found that available optical-computing technology demanded a large and expensive fingerprint system. As a result, the company is redesigning a digital version. Known as the Touchstone system, the palm-sized, self-contained computer is expected to verify fingerprints using a custom algorithm that runs under Microsoft Windows 95 or NT software. The company is also offering an OEM version that can be repackaged to fit inside a standard keyboard, automatic teller machine (ATM), or a point-of-sale terminal.
Tracking criminals
As a systems integrator, Unisys Information Services (Blue Bell, PA) has developed a biometric imaging system for the Middlesex County, Massachusetts, Sheriff`s Department. According to Joycelyn Lyons, Unisys project manager, justice and public safety group, "The biometric imaging system allows identification and tracking of criminals and shares data with local, state, and national agencies."
For the system installation, Lyons` group integrated a system of servers and workstations that connect the state`s jail in Cambridge, MA, and the state`s prison in Billerica, MA. One LiveScan fingerprint scanner from Digital Biometrics Inc. (Minnetonka, MN) is connected to each of twelve 120-MHz Gateway 2000 Pentium-based workstations running under Windows NT software. Four of these workstations are located in the Cambridge facility; the other eight are in Billerica.
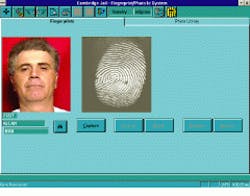
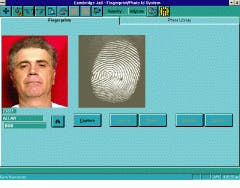
After a criminal`s fingerprint is scanned, it is transferred to a Gateway computer and then digitized by a frame grabber from Integral Technologies (Indianapolis, IN). Next, the image is stored locally and subsequently compared to a flat file database of fingerprints located on a server from NEC Technologies (Washington, DC). To complete the identification process, four NEC algorithms are used for feature extraction, quality checking, database searching, and print matching (see Figs. 1 and 2).
Explains Middlesex County Sheriff Brad Bailey, "The goals are to reduce costs, put fewer criminals back on the streets, and enable Massachusetts residents to enjoy a safer community." The next major development step for Unisys` Lyons is to convert the flat file fingerprint database to a relational database for more comprehensive information searches.
Similar fingerprint systems have been installed by the TRW Systems Integration Group (Fairfax, VA) for the Ohio State Police and for 43 police forces in the United Kingdom (see Fig. 3). The company has also developed encrypted voter cards for the Jamaican government, based on fingerprint verification, to reduce illegal duplication of voter ballots (see Fig. 4).
ATM verification
In another biometric application, Sensar Inc. (Moorestown, NJ) has licensed its iris-identification technology to Citibank Corp. (Los Angeles, CA), where the system is being tested to verify customer identities at ATMs.
The core of the identification system is Sensar`s IrisIdent, a biometric method that uses the unique patterns of the human eye`s iris to verify identity. Using a video camera, the system images a person`s iris, even through contact lenses or eyeglasses. A software program then digitally maps the tissues of the iris, which are about one-sixth of the eye`s surface area. This digital map, which contains a string of 64 characters, is then matched with database files for verification.
Whereas most fingerprinting systems can perform an identification in about 1 s, iris identification takes several seconds. According to Sensar, its system incurs an error rate of fewer than one in 131,578 transactions, making it more reliable and less intrusive than fingerprinting or retinal scanning.
However, Al Forascella at TRW Systems Integration disagrees. "The biggest problem with iris identification is its unreliability. The blood vessels in the eye can change from one day to the next. This has been seen in diabetics, for instance, where a common side effect is eye blood-vessel changes."
Sensar officials believe they have overcome these problems and are ready to address commercial applications. "Citibank is looking at iris identification and other biometric technologies to improve the security of its ATM transactions," said Jim Zeanah, chief technology officer for Citibank`s development division. "The iris provides a huge degree of differentiation in individuals, and, although we are only testing such systems now, there`s a good possibility we will install this equipment in our ATMs," he adds.
REFERENCE
1. Public Attitudes Toward the Use of Finger Imaging Technology for Personal Identification in Commercial and Government Programs, The National Registry Inc., Tampa, FL; www.nrid.com/privacy.html.
FIGURE 1. The biometric imaging system at the Middlesex County, MA, Sheriff`s Department identifies and tracks criminals using fingerprint identification. The suspect`s fingerprint is scanned into the system and then compared to a database of fingerprints. To complete the identification process, four algorithms perform feature extraction, quality checking, database searching, and print matching.
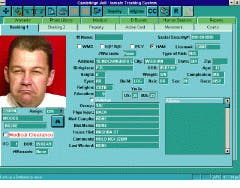
FIGURE 2. After a fingerprint has been matched, the Middlesex County, MA, Sheriff`s Department can call up a computer database relating to the criminal`s history. The database includes prior bookings, outstanding warrants, medical information, and photographs.
FIGURE 3. The TRW National Automated Fingerprint Identification System (NAFIS) allows law-enforcement officers throughout the United Kingdom to capture fingerprints and electronically submit the images to a national database for identification and verification. By the year 2000, the NAFIS is expected to support a database containing fingerprints for more than 6 million persons, as well as 2 million crime scene marks.
FIGURE 4. The Jamaica Elector Registration System (ERS) collects personal data on each citizen of legal voting age either manually or via an electronic registration system. A photograph, signature, and fingerprints are stored in a secure database. The ERS automatically matches the fingerprints to detect fraudulent registrations.
Biometric standards and certification
In voice-recognition systems, several companies are offering programming tools for biometric applications. For example, Novell Inc. (Orem, UT) is providing its Speaker Verification Application Programming Interface (SVAPI) for developers incorporating the technology into networked environments. It is supported by related application programming interfaces (APIs), such as the Microsoft SAPI, a proprietary API for Windows 95 and NT software, S100, a common architecture for developing computer-telephony applications, and Sun Microsystems` JavaSpeech, which is for speech recognition using Java software.
Two groups are also providing testing facilities for checking biometrics. The National Computer Security Association focuses on Internet-related security issues (see www.ncsa.com/). The Biometric Consortium, a US-government-sponsored industry association furnishes a national test center at the San Jose State University Biometric Identification Research Institute (San Jose, CA; see www.vitro.bloomington.in.us:8080/~BC/). The San Jose State University site contains listings of relevant conferences, research papers, and pointers to relevant articles and developers of biometrics, security, and personal identification systems. S. W.